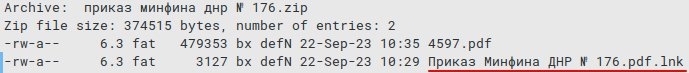
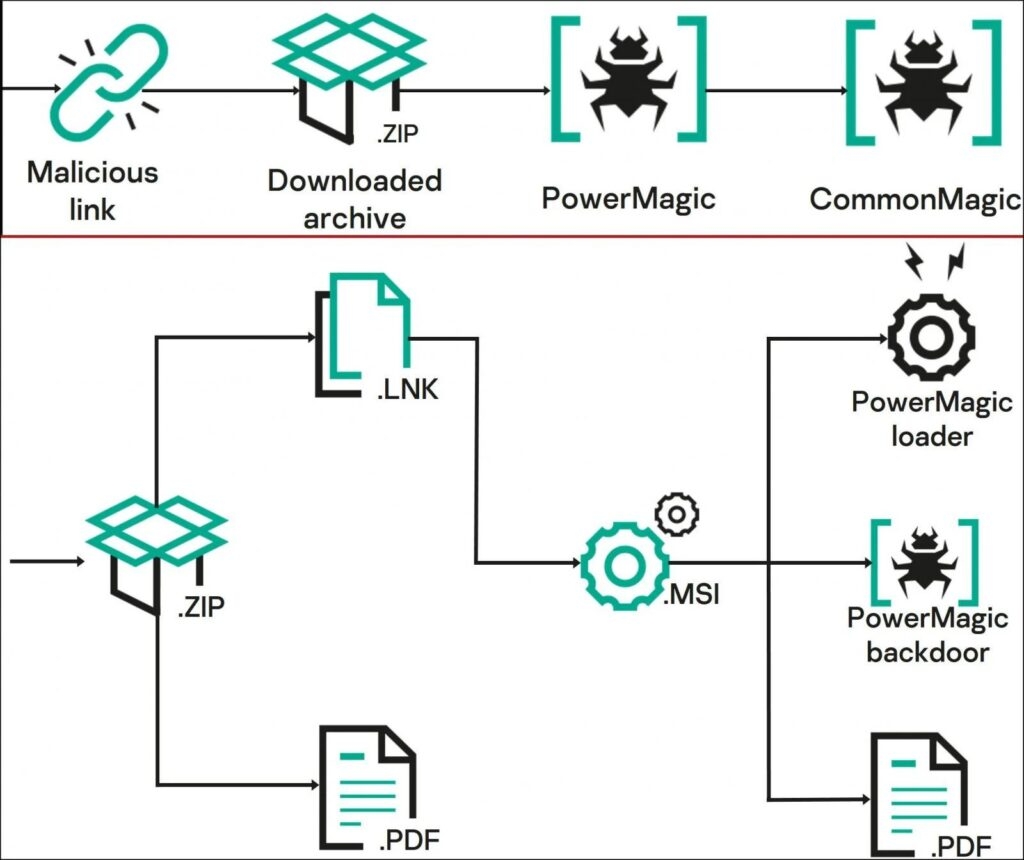
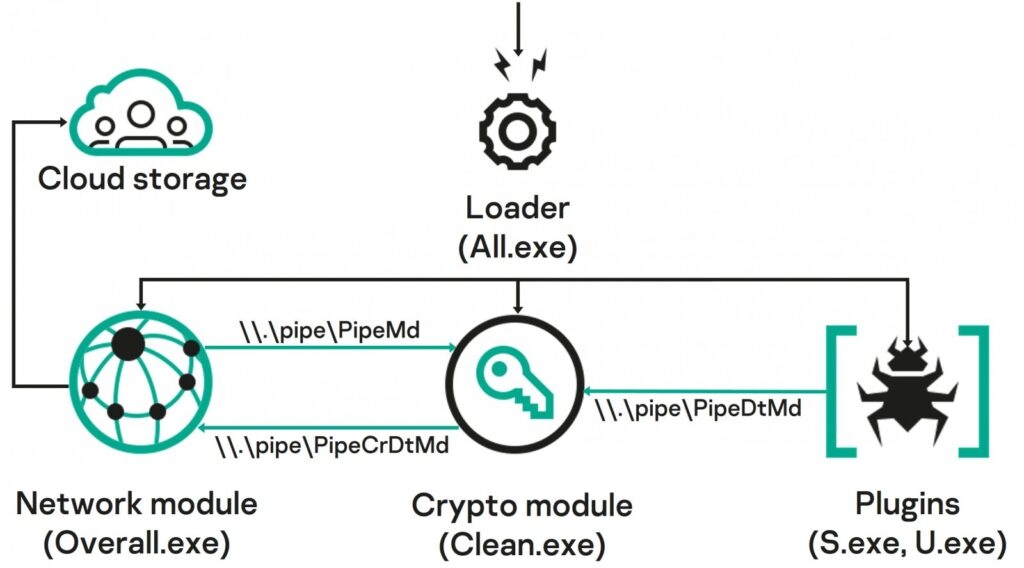
Well, both malware has been in use since at least September 2021, and the attacks that have been continuing to date target agriculture, transportation, and administrative sectors for surveillance motive. Researcher at the cyber security firm mentions that the threat attackers are inclined towards collecting data from Crimea, Donetsk, and Lugansk. As the malware gets inside the victim network, the Common Magic threat attackers can now use individual plugins to steal files and documents such as – DOCX, ZIP, RAR, XLS, XLSX, RTF, ODS, ODT, PDF & more from the USB devices. The malware can also take screenshots every three seconds using the Windows Graphic Device Interface API. The researcher says that the initial infection direction is phishing or a similar method to deliver a URL pointing to a ZIP archive with a malicious LNK file. A decoy document (XLSX, PDF, DOCX) in the archive redirects the user to the malicious activity that started in the background when the LNK file impersonated itself as PDF was launched. According to the security firm, the LNK file activating will make them to infecting the system with a previously unknown PowerShell backdoor which the security researchers named Power Magic after a string they found in the malware code. Read: Bitwarden Password Manager’s Autofill Feature Vulnerable to iframe-based Credential Theft The backdoor interacts with the command and the C2 server to get instructions and upload the results using the Microsoft OneDrive and DropBox folders After the Backdoor infection then; the targets are infected with Common Magic, which is a group of unknown malicious tools that researchers have not seen before these operations. The malicious Common Magic has various elements that begin as standalone executables and use a named pipe to interact. Now as per the security researchers at Kaspersky, the attackers created exclusive modules for the different tasks, for instance, to communicate with the C2 to encrypt & decrypt traffic from the command server, thus stealing documents, and files and taking screenshots. Not only this, but the exchange of data is also done through the OneDrive folder, and the files are then encrypted using the RC5Simple, an open-source library with a custom sequence – Hwo7X8p at the start of encryption. With that being said, the malicious malware or the technique seen in the Common Magic isn’t difficult or something innovative. A string of infections concerning malicious LNK files in the ZIP archive has been observed with multiple threat attackers. A similar technique was observed in the ChromeLoader campaign that was dependent on a malicious LMK to execute a batch script and extract the content of ZIP respiratory to fetch the final payload. Although the nearest to the Malicious CommandMagic method is an attacker that was tracked YoroTrooper who was engaged in cyberspying activity via using phishing emails that delivered malicious LNK files and impersonated PDF documents housed in a ZIP or RAR archive Despite the non-customary approach, the malicious malware, the malicious malware has been pretty successful. Although the malicious malware seems to have started in 202. As per the security researchers, the threat actors intensified their campaigns last year and are still continuing to do so. Read: Fortinet Cyber Security Update Fails; Zero-Day Exploited by Threat Actors